Exposure Notifications
Contact tracing is one of the most important measures to fight the spread of the Corona Virus in the ongoing pandemic.
This must be done as fast as possible to get ahead of the virus and prevent infected persons from spreading the virus further.
Contact tracing is usually done by health offices via telephone.
Smartphone apps can be used to accelerate contact tracing because they can inform potentially infected persons more quickly.
Apps can still work at the same speed when a health office has reached its capacity limit.
App-based contact tracing is usually done via Bluetooth Low Energy. Smartphones indicate their presence to other smartphones
by sending pseudonymous IDs which are then received and stored by other smartphones.
These IDs can then be matched against a list of known infected IDs to determine the risk of infection for the user of a smartphone.
There are two different approaches to implement this:
The Exposure Notification protocol works like this: Every smartphone sends Bluetooth Low Energy beacons four times per second and listens for the beacons of other smartphones. Upon reception of a beacon the signal-strength is used to determine the distance between sender and receiver.
(The original name of this protocol is 'DP-3T' - you can find a more detailed explanation of how this works here in this nice comic.)
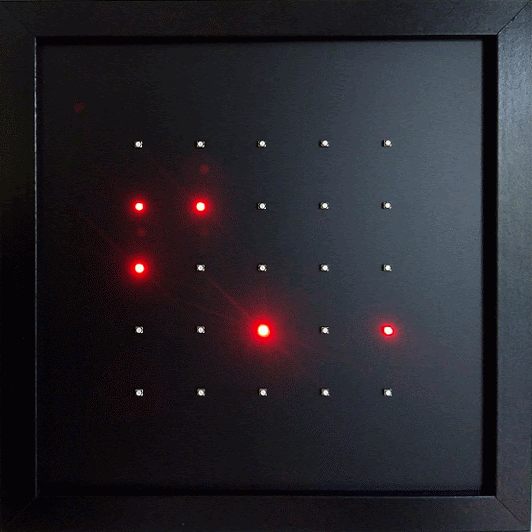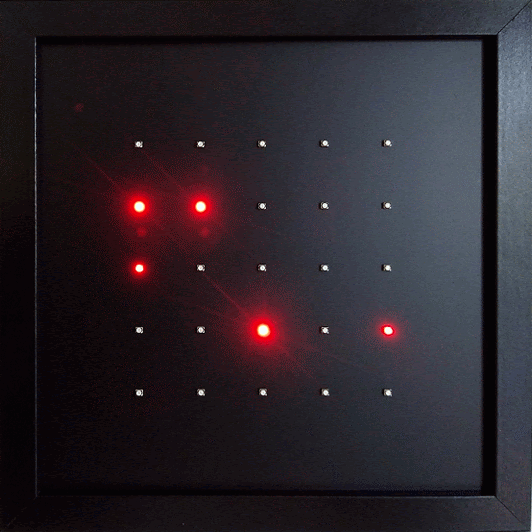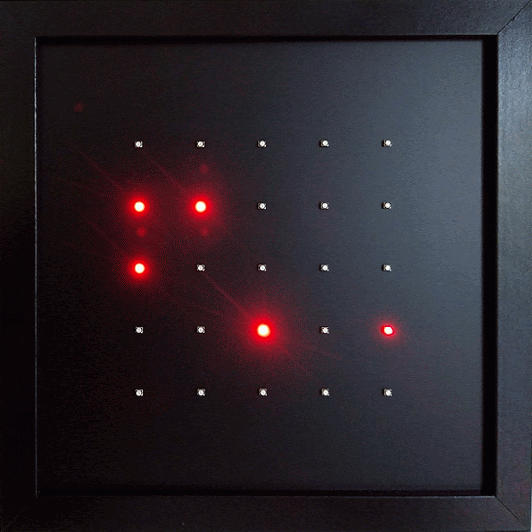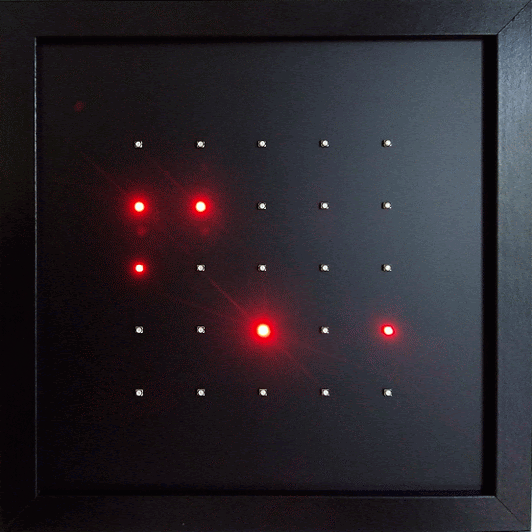
Exposure Notifications receives the Exposure Notification beacons just like a smartphone. 25 red LEDs visualize the pseudonymous IDs. Each LED represents one ID. The LED brightness indicates the signal strength - and therefor the intensity of a human contact as preceived by a smartphone.
There are two different approaches to implement this:
- Apps using a centralized approach send all IDs of contacts to a central server. The server then checks for matches to determine the infection risk for the smartphone user. This approach is a privacy nightmare because the server operator is able to track all contacts between all IDs.
- Apps using a decentralized approach never send IDs of contacts to a central server. Instead the smartphone app downloads a list of infected IDs from the server and matches the list of seen IDs against this list. This approach is privacy preserving because the server operator is unable to track any contacts.
The Exposure Notification protocol works like this: Every smartphone sends Bluetooth Low Energy beacons four times per second and listens for the beacons of other smartphones. Upon reception of a beacon the signal-strength is used to determine the distance between sender and receiver.
(The original name of this protocol is 'DP-3T' - you can find a more detailed explanation of how this works here in this nice comic.)
Exposure Notifications receives the Exposure Notification beacons just like a smartphone. 25 red LEDs visualize the pseudonymous IDs. Each LED represents one ID. The LED brightness indicates the signal strength - and therefor the intensity of a human contact as preceived by a smartphone.
After the Corona-Warn-App became available nerds in Germany quickly started wondering how widespread the app is.
It would be nice to see the number of IDs (and thus app users) in the vicinity.
Today there are several smartphone apps which show the number of active IDs, but the foundation of Exposure Notifications
is a program which has been implemented for the BBC micro:bit: the microbit-corona-scanner. More details about this can be
found in the next section.
We're all potential vectors during a pandemic. We're reminded of this inconvenient fact again and again - for example when we see a person wearing a mask. Contact tracing Bluetooth beacons warn other smartphones about our presence - similar to a lighthouse warning ships. But we're unable to perceive these signals directly with our human senses. Instead smartphones receive these silent warnings, estimate our physical distance and rate the infection risk in the background.
The microbit-corona-scanner and Exposure Notifications grant us a glimpse into the silent communication between machines. The silent warnings become visible.
We're all potential vectors during a pandemic. We're reminded of this inconvenient fact again and again - for example when we see a person wearing a mask. Contact tracing Bluetooth beacons warn other smartphones about our presence - similar to a lighthouse warning ships. But we're unable to perceive these signals directly with our human senses. Instead smartphones receive these silent warnings, estimate our physical distance and rate the infection risk in the background.
The microbit-corona-scanner and Exposure Notifications grant us a glimpse into the silent communication between machines. The silent warnings become visible.
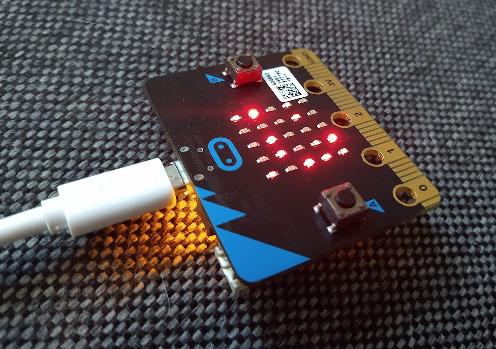
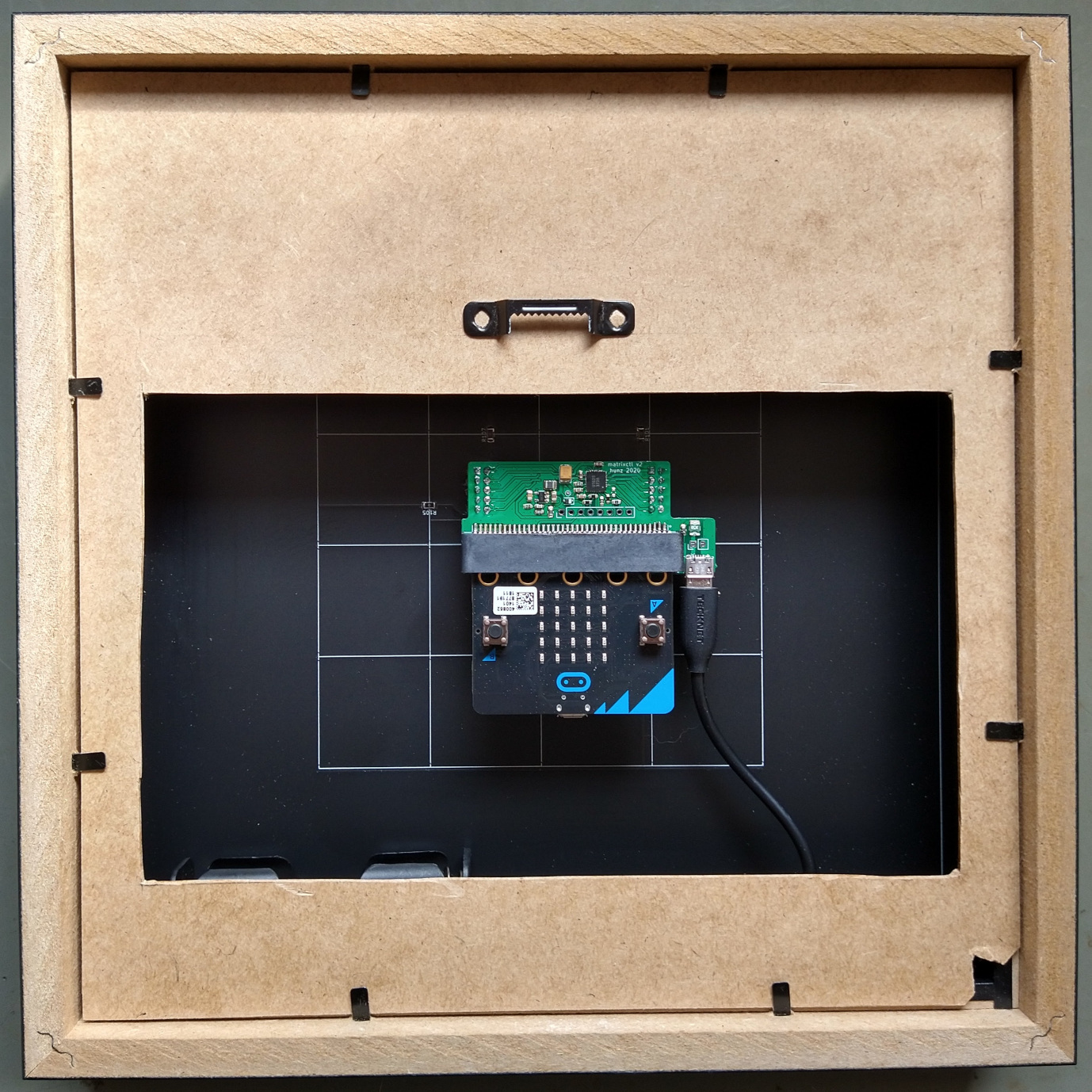
The groundwork of Exposure Notifications is the microbit-corona-scanner project. microbit-corona-scanner is Open Source, runs on a BBC micro:bit and works just like Exposure Notifications, but with more features. Different visualisation modes are available, as well as acoustic output.
It's a tiny, portable version of the project - perfect for further experiments.
Here you can find a tutorial and usage instructions for the microbit-corona-scanner.
If you have some experience with electronics and SMD soldering you can also build Exposure Notifications (or a derivative) yourself. The design is Open Source as well. You'll need a common RIBBA-frame from IKEA. A BBC micro:bit and two custom printed circuit boards are required as well. You can find the design files for these PCBs here. The microbit-corona-scanner needs to be installed on the micro:bit. The regular version already includes the Exposure Notifications mode: the additional boards will be detected and put into operation automatically.
Corona contact tracing apps which rely on the Exposure Notification protocol
cannot be abused to monitor contacts between users of such apps.
Contact data is never sent to a server. Signals sent via Bluetooth are pseudonymous IDs.
These can only be received in the vicinty of the sending smartphone.
The IDs change every ten to twenty minutes and they cannot be attributed to certain persons.
IDs of observed contacts are encrypted and stored for 14 days only in the smartphone of the user.
The smartphone downloads a list of infected IDs once a day and checks the own contact log for matches.
If a match exists the infection risk is calculated by the smartphone.
Even if you are infected and decide to warn others via the app, no personal data is transmitted. Just your pseudonymous IDs are added to the list
of infected IDs.
You can find a more detailed explanation of how this works
here in this nice comic.
Exposure Notifications or the microbit-corona-scanner can be used to examine and verify certain aspects of the described operating mode. Each LED represents one ID. If the ID disappears the associated LED will go out. To identify the LED associated with your own smartphone you can temporarily disable Bluetooth on the phone. The corresponding LED will go out. It will light up again as soon as Bluetooth is turned back on again. The pseudonymous ID changes every ten to twenty minutes. When this change occurs the previous ID disappears and a new ID emerges. The LED for the old ID expires and a new one lights up. Range and strength of the Bluetooth signal can be estimated by observing the LED brightness. Once an ID disappears the brightness of corresponding LED starts to decline and the LED expires completely after two seconds.
Exposure Notifications or the microbit-corona-scanner can be used to examine and verify certain aspects of the described operating mode. Each LED represents one ID. If the ID disappears the associated LED will go out. To identify the LED associated with your own smartphone you can temporarily disable Bluetooth on the phone. The corresponding LED will go out. It will light up again as soon as Bluetooth is turned back on again. The pseudonymous ID changes every ten to twenty minutes. When this change occurs the previous ID disappears and a new ID emerges. The LED for the old ID expires and a new one lights up. Range and strength of the Bluetooth signal can be estimated by observing the LED brightness. Once an ID disappears the brightness of corresponding LED starts to decline and the LED expires completely after two seconds.